Strengthening Background Checks for Government-Related Roles with OSINT


Every position of trust in government, defense, or critical infrastructure begins with verification. Background checks form the backbone of that trust, ensuring that individuals granted access to sensitive data and facilities, or in critical decision-making roles meet strict standards of reliability and integrity. Such checks are essential for safeguarding institutions against insider threats, data leaks, and conflicts of interest.
In this article, we explore how open-source intelligence (OSINT) enhances government background checks by adding context, depth, and real-time visibility to traditional vetting methods, and how publicly available data—from social media activity to domain records—helps investigators validate identities, uncover hidden risks, and make faster, better-informed clearance decisions.
Across governments worldwide, background checks are designed to assess an individual’s trustworthiness, loyalty, and suitability for roles tied to national or organizational security. While procedures differ between countries, most follow a similar structure that combines administrative verification with behavioral assessment.
Typical stages include:
Government background investigations are not simply administrative—they are the foundation of trust in public institutions, safeguarding against insider threats, data leaks, and conflicts of interest.
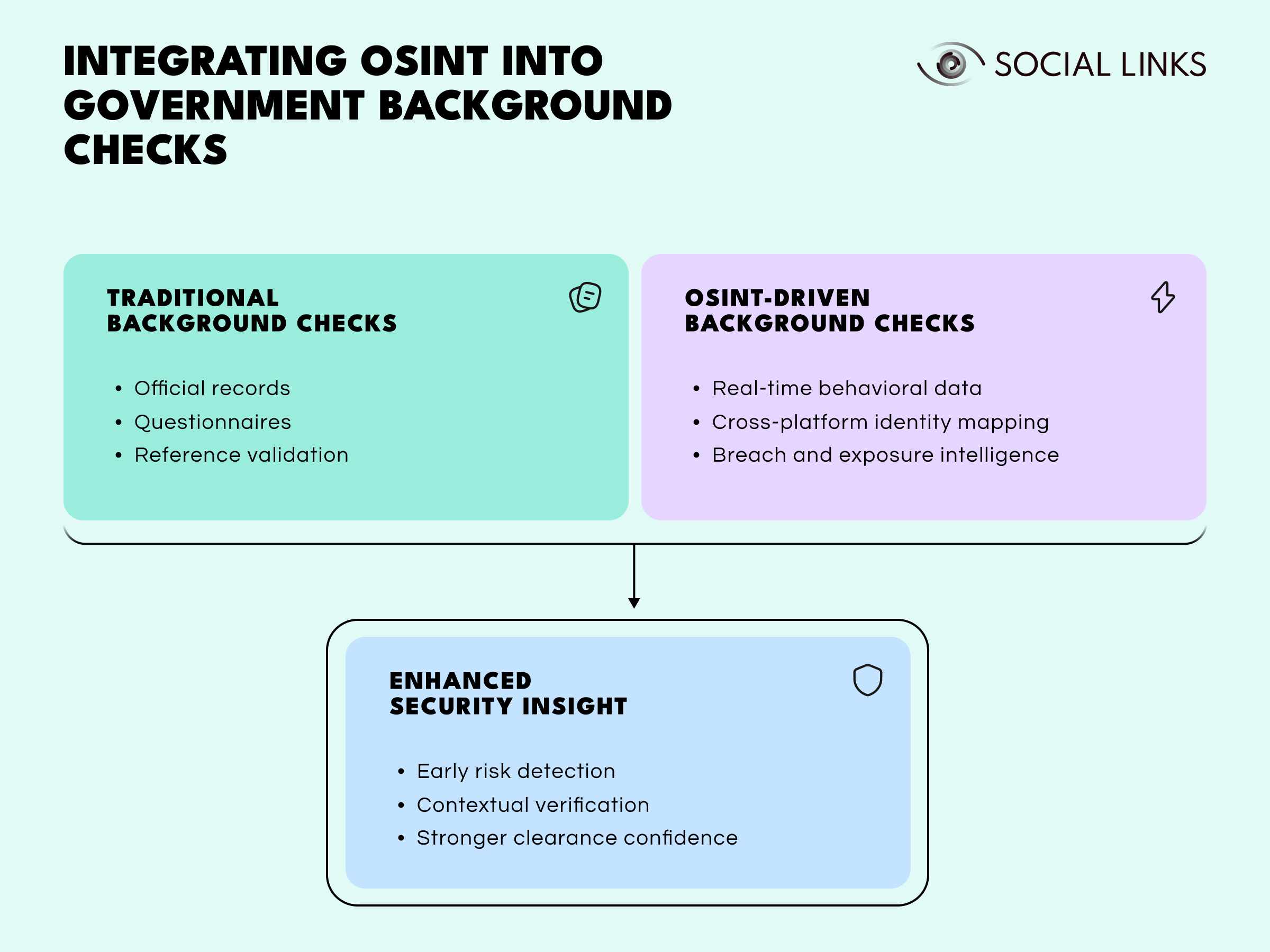
Traditional background checks rely heavily on official databases and personal disclosures. OSINT complements this by adding real-time, context-driven intelligence—filling visibility gaps that closed records cannot.
OSINT contributes by:
When combined with traditional intelligence methods, OSINT transforms background checks from static verification into dynamic analysis—providing early warning signals and a richer understanding of context.
Security vetting within the military and defense sectors requires even greater scrutiny. Personnel, contractors, and civilian partners are often granted access to highly sensitive data, systems, or facilities—making background integrity checks critical.
In defense-related investigations, OSINT helps to:
By correlating open-source information with classified assessments, defense and intelligence agencies can strengthen both insider threat prevention and supply chain assurance—ensuring every actor in the ecosystem can be trusted.
Comprehensive vetting requires multiple data layers, combining closed records with open data. OSINT enhances each category by adding context and cross-verification.
Key categories include:
These layers allow investigators to see beyond the résumé—connecting technical, behavioral, and social signals into a complete risk profile.
While OSINT increases efficiency and visibility, it also requires disciplined methodology to avoid overreach or error.
Key challenges include:
Best practices for investigators include:
Solutions such as Social Links Crimewall enable investigators to automate data discovery, map digital relationships, and visualize entity linkages—all within frameworks that comply with data protection and investigative standards.
As digital presence becomes inseparable from personal identity, OSINT will continue reshaping how governments and defense institutions verify personnel. Open data doesn’t just confirm facts—it contextualizes them.
By bridging technical records with behavioral insight, OSINT allows for predictive—not just reactive—vetting. It helps agencies identify emerging risks, detect compromise, and maintain trust in sensitive ecosystems long after the initial investigation is complete.
Incorporating OSINT into government background checks represents a natural evolution of national and organizational security. It unites the human layer—behavior, digital footprint, and reputation—with technical and legal verification, delivering a holistic view of trustworthiness.
Whether assessing civil servants, defense contractors, or private sector partners, OSINT empowers vetting authorities to act with precision, transparency, and speed—reinforcing the security of institutions worldwide.
OSINT expands traditional checks by adding real-time visibility into online behavior, affiliations, and exposure risks. It helps investigators verify identities and detect inconsistencies faster and more accurately.
Depending on the country, national security agencies, defense ministries, or authorized vetting bodies integrate OSINT tools into their investigative workflows, especially for roles that require a security clearance.
Investigators review registration data, social media, breach records, and public databases to verify claims, uncover hidden links, and evaluate potential risks.
Yes. OSINT relies solely on publicly available, legally obtained information. Responsible use requires compliance with privacy, data protection, and investigative standards in each jurisdiction.
For defense contractors, OSINT helps confirm legitimacy, detect potential foreign influence, and ensure that individuals or organizations meet security and compliance criteria before access is granted.
Want to see how OSINT streamlines modern vetting workflows? Book a personalized demo with one of our specialists and discover how SL Crimewall helps investigators verify identities, map affiliations, and detect hidden risks—all within a single, compliant intelligence platform.