The Dark Web Demystified: A Practical Guide to Darknet Investigations


It has a notorious reputation to be sure. Yet the common perception of the Dark Web purely as an arena for nefarious enterprise overlooks the double-edge nature of the beast. While its mix of anonymity and obfuscation does indeed make it a haven for fraudsters peddling fentanyl, stolen creds, and zero-days, it is also the hunting-ground par excellence for investigators of many kinds.
So today we want to set the definition straight and give a practical guide for those who understand the remarkable investigative potential of the internet’s infamous underbelly, and want to maximize its utility in their work. Read on to learn the reasons for the Dark Web’s importance as a resource, key approaches to running effective researches, essential tools, real-world case studies, and more.
Forget Hollywood montages of green code rain and hooded figures. The Dark Web is simply any corner of the internet that requires special software or credentials to reach, most famously via the Tor network, but also I2P, Freenet, and walled-garden IRCs. Pages don’t index on Google, domains end in .onion (or .i2p, etc..), and traffic pinballs through encrypted relays until location data is basically radioactive dust.
Because reputation is the only real currency down there, markets and forums rise and fall fast; permanent storefronts are the exception, not the rule. In other words, the Dark Web is part bazaar, part ghost town, forever rebuilding itself just out of reach.
The aftermath of every major breach eventually drips onto an .onion board—ransomware gangs auctioning internal docs, insider traders seeking buyers, hacktivists leaking troves “for the lulz”. If you’re in cyber-defense, brand-protection, law enforcement, or even due diligence, darknet monitoring is the fastest early-warning system you’ll ever deploy. It’s also a rich mine of intelligence for:
Attribution Clues: Chat-handle overlaps, PGP key re-use, and linguistic tells.Pre-Sale Data Leakage: Employee logins, NDAs, and prototypes posted before they hit public paste bins.Threat-Actor Chatter: Which verticals they plan to hit next, what exploits they’ve beta-tested, who’s hiring money-mules, and so on.
It’s a jungle out there so you don’t want to go in green—here are our recommended approaches to avoid the most common pitfalls and make the most of your endeavors.
You need an isolated VM (Tails OS, or qubes OS if you are a maniac), and even better, an air-gapped laptop. Full-disk encryption, no personal accounts, a fresh operating system image for every mission. Assume compromise is inevitable; plan data exfil paths accordingly.
A rookie mistake is to load Tor and immediately start clicking around with default browser fingerprints. Harden your user-agent, disable JavaScript, and avoid hefty downloads. If you absolutely must interact (like posting in a forum or PM a vendor) do it through a sock puppet that can disappear without wrecking your day job, and without killing the reputation you may have built with other personas.
Treat the Dark Web like a city without streetlights—you’ll want a map before you start walking. Onion “search engines” such as Ahmia, Haystak and Phobos work like a dim-bulb Google: results are patchy, but they at least tell you which neighborhoods exist (to be honest, we really don’t use or trust them).
Then you have index pages like tor.taxi or dark.fail, curated link lists whose maintainers vet each URL, flag scams, and track when sites move or die. Beyond those staples, whole communities keep living spreadsheets of ransomware-gang leak sites, credential-trading forums, carding shops, and whistle-blowing dropboxes—you’ll find them on some Telegram channels, websites or buried in Git repos.
Whatever breadcrumb you follow, never assume the first .onion is legit. Typosquats are rampant and often booby-trapped with phishing pages or malware “patches”. Before you click past the home page, make sure you:
Mind the version history. Dark-Fail, for example, logs historical URLs for big markets; a sudden domain change without an accompanying signed notice is an amber flag.
Crypto wallets, PGP fingerprints, vendor rating IDs, these threads weave a tapestry. A wallet reused across marketplaces can shortcut months of analysis. Pair those traces with off-site mentions (Telegram, Discord, Mastodon clones) and patterns emerge: delivery times, price fluctuations, grudges between rival crews.
Time stamps, onion links, screenshots, chat transcripts. Collect first, sanitize later. Dark-web content vanishes overnight; your only constant is the evidence you seize in real time.
You won’t find a single “darknet investigation tool” button. Instead, practitioners stitch together their own kit:
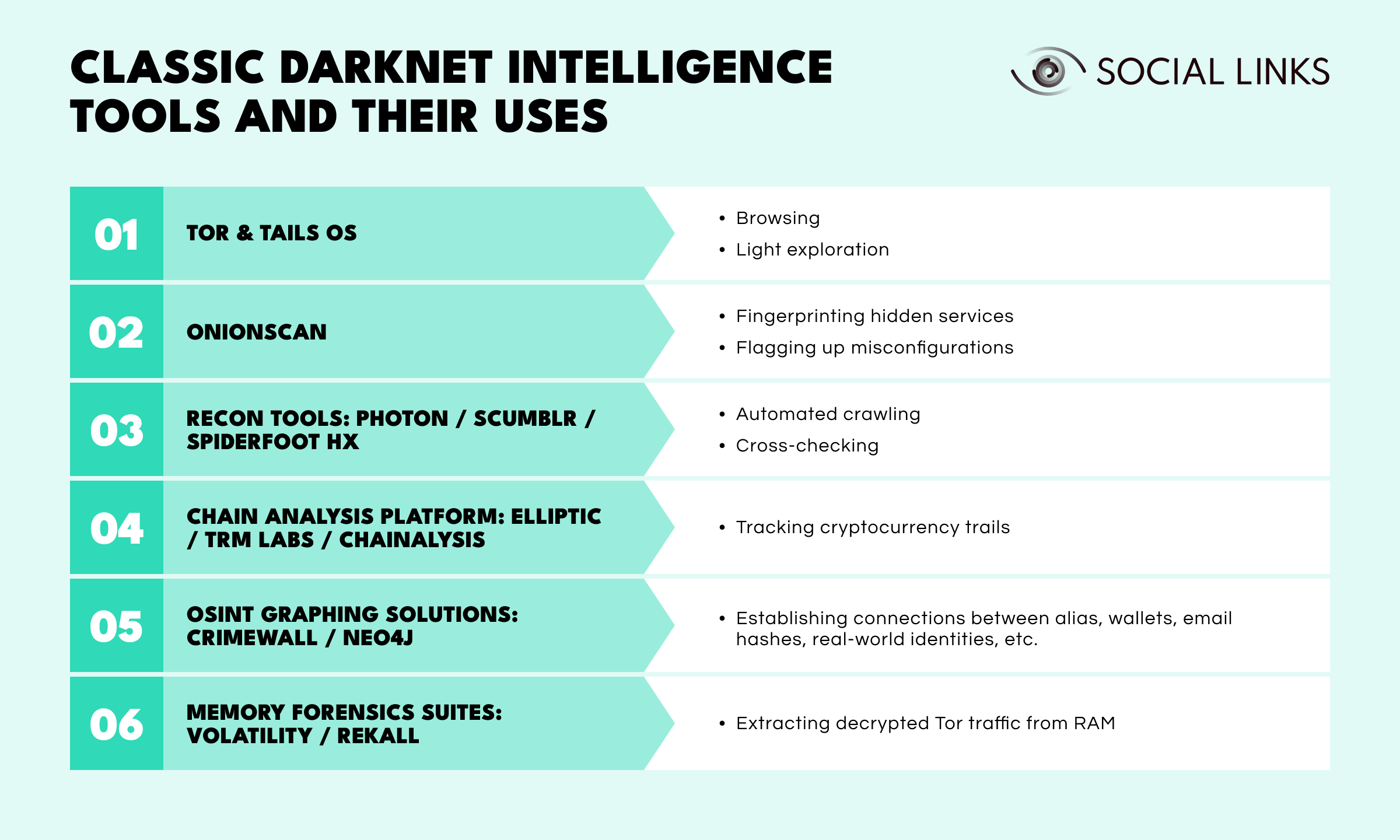
Pick what suits the case. Sometimes your VM, Tor and a Notepad is enough.
OSINT graphing solutions: Crimewall, or plain-vanilla Neo4j, for stitching aliases to wallets, to email hashes, to real-world identities.
Memory forensics suites (Volatility, Rekall) when you seize a suspect’s live system and need to pull decrypted Tor traffic out of RAM.
Pick what suits the case. Sometimes your VM, Tor and a Notepad is enough. And once darknet observations accumulate, structuring them inside a unified OSINT framework dramatically improves attribution speed, hypothesis testing, and case reporting — especially when investigations go beyond a single platform or identity.
Once you scoop data, you need to preserve and present it. Chain-of-custody standards still apply, even if the evidence lives behind triple-layer onion routing. We recommend:
Courts have upheld dark-web evidence when collection is transparent and reproducible. They’ve also tossed entire cases when an analyst “forgot” to note that JavaScript was left on, potentially altering server-side content. Details win trials.
In 2022, the “Genesis Market” takedown hinged on an undercover agent buying stolen browser-fingerprint bundles, then pivoting via wallet analysis back to a Ukrainian-based admin who reused a Steam handle from his teenage Counter-Strike days.
This style of multi-layered attribution isn’t possible without rigorous digital footprint investigations, where usernames, wallet reuse, metadata, and external chatter are correlated into a cohesive identity model — letting analysts bridge the gap between darknet anonymity and real-world personas.
In 2024, a French health-care provider foiled a ransomware double-extortion when darknet scanners spotted a teaser dump of patient data 48 hours before full publication; their IR team negotiated from a position of knowledge, cut the ransom by 90%, and had legal ammo to trigger cyber-insurance clauses.
Earlier this year (2025), Interpol’s “Operation SpecTor” correlated a single PGP block-quote across three onion forums, tracing it to a Dutch vendor whose home server leaked its public IPv6 via misconfigured Nginx. One breadcrumb is all it takes.
The Dark Web moves faster than the law, but you still have to play on its board. Consult your legal team early and keep the following in mind:
Passive Monitoring: Browsing, indexing, scraping, tends to be lawful in most jurisdictions, but always verify local statutes. And be very careful if you are dealing with CSAM content—but that’s another story.
Active Engagement: Posing as a buyer or initiating a deal, often crosses into undercover territory you’ll need warrants or at least legal counsel.
Malware Possession Laws: These are tricky as downloading exploit kits “for research” might still be criminal if intent isn’t crystal-clear.
Darknet investigation may look glamorous, but it’s equal parts slog and stress. Expect those Tor services you are investigating to disappear overnight, the necessity to pose as a 15-year-old anime fan just to get reputation on a forum, and long stretches of staring at hexadecimal wallet IDs. The payoff? Stopping a breach before it headlines, unmasking a child-exploitation ring, or simply sleeping better because you know what’s lurking in the shadows around your brand.
If you’re new, start small: monitor a single marketplace for mentions of your company’s domain. Graduate to wallet tracing and interacting with actors. Eventually, maybe you’ll run a full takedown op with three-letter agencies, but mastery begins with the first cautious click.
The Dark Web isn’t some mystical underworld—it’s just another place on the internet. Navigate with the right prep, the right mindset, and a solid ethical compass. Tight your OPSEC, hash your logs, and remember: down here, curiosity doesn’t kill the cat, but sloppiness might.
If you want to learn more about how Social Links can revolutionise your darkness researches, get in touch. Just follow the button below and we'll set up a personalized demo so you can see exactly how we can help your workflows.