Top 10 OSINT Tools, Products, Solutions, and Software for 2026


Open-source intelligence has exploded over the years, shifting from a niche capability into an indispensable component of modern security, fraud prevention, and investigative work. With attacks getting ever more targeted, digital ecosystems becoming more complex, and threat actors moving faster than ever, organizations can no longer rely on isolated searches or manual review. The right OSINT tool doesn’t just retrieve data—it gives analysts the scale, structure, and visibility they need to act with confidence.
In this article, we present a carefully curated selection of standout OSINT tools for 2026. Each tool is evaluated for its real-world utility—from identity tracing and infrastructure mapping to fraud detection and social-media forensics—giving you a comprehensive snapshot of what great solutions are out there now and how they can fit into your investigative stack.
In 2025, organizations faced one of the most volatile threat environments on record. Phishing volumes surged past one million attacks by the end of Q1, with criminals now sending millions of QR-code phishing emails daily. Payment and banking services were disproportionately targeted, representing nearly 31% of all attacks, and BEC wire-transfer fraud jumped 33% quarter-over-quarter, showing just how quickly threat actors can adapt and bypass defenses.
Breaches also remained financially punishing. The global average cost settled at $4.44M—slightly lower than last year—but the United States surged to a record $10.22M due to rising regulatory and response costs. AI-related incidents added new pressure: 97% of breached organizations lacked proper AI access controls, leading to broad data exposure and operational disruption. Meanwhile, shadow AI continued to inflate losses, adding an average $670K when unapproved AI tools were involved.
As organizations confront these realities, intelligence has become the defining advantage. And that begs the question—what tools can help you harness that advantage in 2026? Read on to find out.

A next-generation all-in-one OSINT investigation platform, SL Crimewall is built to handle the full lifecycle of digital investigations—from data collection to final reporting. It stands out for its integrated environment, where teams can collaborate, pivot across data types, and scale their workflows without switching tools.
Collaborative Casework. Crimewall’s workspace is designed for multi-analyst investigations. Teams can share cases, track evidence, annotate findings, and maintain access-controlled visibility across departments—ideal for complex, long-running cases.
Extensive Open-Source Coverage. The platform provides structured access to real-time data across social media, messengers, corporate databases, darknet sources, blockchains, and more. Its proprietary search methods help analysts pull high-precision results without manual filtering.
Process Automation. From bulk data extraction to scheduled monitoring and scripted processing, Crimewall minimizes routine workloads. Analysts can automate repetitive tasks and focus on interpretation rather than manual collection.
Advanced Visualization & AI Analysis. Graph views, footprint visualizations, and built-in link analysis help users uncover hidden connections. AI-driven enrichment and NLP models further speed up entity recognition, lead discovery, and behavioral mapping.
Reporting Capabilities. Crimewall offers flexible report exports, allowing users to compile structured case summaries, timelines, and evidence packages in a few clicks.

One of the most established and widely used OSINT and link-analysis tools. Maltego shines when you need to map relationships—between people, domains, infrastructure, social profiles, and more—in a visual, graph-based interface.
Transform Hub. A robust marketplace of data integrations gives analysts plug-and-play access to dozens of providers for identity, infrastructure, and corporate intelligence.
High-Scale Graphing. The solution handles graphs with up to a million entities using multiple layouts (hierarchical, organic, block, and circular) for deeper pattern recognition.
Rapid Data Fusion. Point-and-click pivots and regex-based entity detection make it easy to merge disjointed datasets.
Multi-User Collaboration. Analysts can work together on shared graphs and annotate investigative steps throughout.

A top-tier threat-intelligence platform that blends real-time data feeds, darknet monitoring, and predictive analytics, giving security teams proactive visibility on emerging risks.
Massive Intelligence Corpus. Users can track billions of domains, hundreds of millions of IPs, vulnerabilities, leaked credentials, and organizational assets.
AI Classification Engine. NLP is used to categorize and relate global intelligence signals across 13+ languages.
Purpose-Built Modules. Preconfigured modules deliver quality threat intelligence, brand protection, vulnerability intelligence, and more streamlined investigations.
Use-Case Alignment. Intelligence is packaged around practical workflows, helping organizations quickly address high-impact vulnerabilities.

A powerful data-analysis and visualization suite frequently used by law enforcement, national-security bodies, and fraud investigators. i2 excels at structured data analysis, timeline visualizations, and link analytics across large datasets.
Flexible Modeling. The system can support advanced graphing, geospatial mapping, and timeline analysis.
Parallel Querying. Data can be pulled from multiple connected sources simultaneously.
Rich Integrations. The solution can handle structured and unstructured data from countless systems.
Collaboration & Customization. Shared access, drag-and-drop logic, and customizable layouts allow teams to tailor their analysis style.
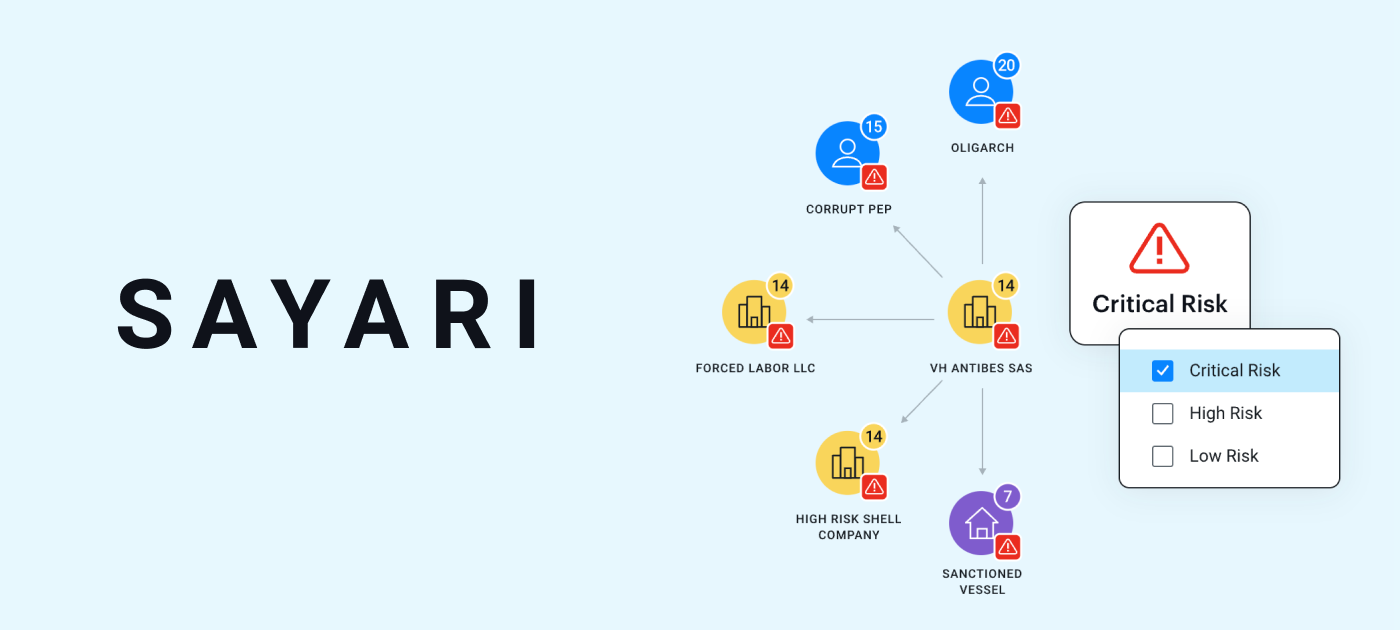
Built for corporate-intelligence use cases, Sayari specializes in mapping corporate ownership, supply chains, and global entity networks—ideal for due diligence, AML, and compliance workflows where understanding corporate relationships is critical.
Massive Corporate Dataset. Billions of state records gathered from thousands of registries worldwide.
Structured Entity Mapping. Directors, companies, subsidiaries, and filings can be cleanly linked into navigable graphs.
Risk Identification. Negative exposure, procurement vulnerabilities, and opaque ownership structures can be flagged.
Ontology-Backed Organization. A carefully designed data model keeps complex corporate relationships intuitive.

A deep people-search engine focusing on identity intelligence, Pipl helps users correlate emails, usernames, phone numbers, and aliases across public and proprietary sources—a go-to tool for fraud analysts, compliance officers, and identity verification teams.
Deep Search Coverage. Data from the Surface and Deep Web, public records, and proprietary sources can be readily accessed.
Global Index. Identity data spanning multiple countries can be aggregated to support cross-border investigations.
Recursive Matching. Automated cross-checking validates data points against multiple sources.
Flexible Scaling. Streamlined onboarding and rapid data retrieval support high-volume workflows.

Known as the “search engine for internet-connected devices”, Shodan gives security teams eyes on exposed servers, IoT devices, webcams, and other online assets. It’s especially useful for external infrastructure reconnaissance, vulnerability assessments, and footprint discovery.
Exposure Mapping. The system can identify open ports, misconfigured services, industrial systems, webcams, and IoT devices.
Historical Snapshots. Historical infrastructure data is provided, facilitating support attribution and incident reconstruction.
Risk Scoring. Vulnerable or high-risk assets across organizations or IP ranges can be flagged.
Integration Flexibility. The solution is compatible with CTI workflows, SIEMs, and red-team tooling.

A heavyweight analytics platform often used by government and large enterprises. Gotham integrates massive, multi-source datasets—OSINT, structured corporate data, internal systems—enabling complex investigations, threat modeling, and strategic intelligence.
Unified Data Environment. Vast, heterogeneous datasets can be seamlessly integrated into a consistent operational model.
Sensor Tasking. AI-assisted orchestration of drones, satellites, and edge sensors facilitate intelligence collection.
High-Security Design. The system is designed for environments where data protection and access control are paramount.
Mixed-Reality Operations. Virtual collaboration features support mission planning and real-time coordination.

A specialist tool for blockchain and cryptocurrency investigations. Elliptic helps trace funds, identify wallet ownership, monitor illicit flows, and expose connections between financial instruments or suspicious entities—increasingly relevant in fraud, AML, and crypto-crime contexts.
Wallet Attribution. Owners, intermediaries, and transactional behavior can be identified across chains.
Automated Risk Monitoring. Links to laundering, terrorist financing, and sanctioned entities can be detected.
Graph-Based Crypto Tracing. Visual transaction paths allow users to rapidly collect evidence.
Holistic Coverage. Entire crypto ecosystems can be mapped to reveal broader patterns and hidden networks.

A reverse-image search engine and facial recognition tool. By uploading a photo, investigators can discover where it appears across the web, track image reuse, and detect possible impersonation or identity fraud—valuable in social-media investigations, brand security, and identity verification.
Simple Interface. By just uploading an image, users can immediately find visually similar matches across the internet.
Monitoring Alerts. New appearances of faces or images can be tracked in real time.
Precise Source Identification. The exact appearance location of a given photo can be pinpointed, supporting verification or takedown actions.
Batch Processing. Multiple images can be searched and monitored at once.
As we roll into 2026, the need for OSINT is as clear as ever. As attackers and their approaches evolve, investigators and security teams must adapt quickly. The tools above represent some of the most effective, widely used, and versatile platforms available now, covering social media, infrastructure, finance, darknet intelligence, identity verification, and analytics.
So let’s harness these great technologies. In a world where a single phishing campaign, misconfigured server, or anonymous wallet can cost millions, visibility and speed are your best defense.
Want to streamline your investigations with unified data gathering, advanced link analysis, and real-time collaboration? Book a personalized demo and see how SL Crimewall integrates a wide range of OSINT technologies and sources into a single user-friendly workspace.