Top 7 OSINT Methods to Transform Any Investigation

While OSINT work and open data research are often considered technical, they really don’t have to be. In this article, we wanted to take readers through our top pick of Social Links open-source intelligence methods that anyone can – and should – try to revolutionize investigation processes, delivering highly successful results regularly.
Below, you'll find seven tried-and-tested OSINT search methods that don't require specialist skill or knowledge, yet the results could be transformative for any investigation using them. All of them are available in our full-cycle OSINT investigation platform, SL Crimewall.
So, let’s take a look!
So, imagine you’re starting an investigation with just two data points: a picture and a name/alias. Perhaps you found both inputs from a single source, such as Telegram, or maybe you have the data from two separate sources. Trying to find someone on social media with just a name is extremely time-consuming since any single appellation may have hundreds of variants out there. But by matching a name and picture, the profile you need can be instantly found.
Search by Face and Name/Alias search method uses real facial recognition. This means the system doesn’t just match two digital copies of the same image; it understands the person's biometrics and finds all pictures corresponding to this data. It’s possible to find someone even if they have physically changed since the photo was taken – i.e., they have grown up or changed their look. And this feature works across all major social media platforms such as X (ex Twitter), TikTok, LinkedIn, Telegram, etc.
Let’s say we have a Telegram profile already containing both a picture and an alias, and we want to find the subject’s profile for all their other social media accounts. We simply run Search by Face and Name/Alias methods simultaneously via the Search Profile in Other Networks set. SL Crimewall will return the exact profile we need for each source without showing extraneous namesakes. You can run the search methods individually if there is one particular source you are looking for.
Ok, moving to the second instance, we have a photo and a name from different sources. We first need an entity to combine the input data, Search Profiles by Face. Next, we enter the data into the relevant fields with a URL for the image. We now run the same methods, et voila – we’ll get all the profiles linked to our subject.
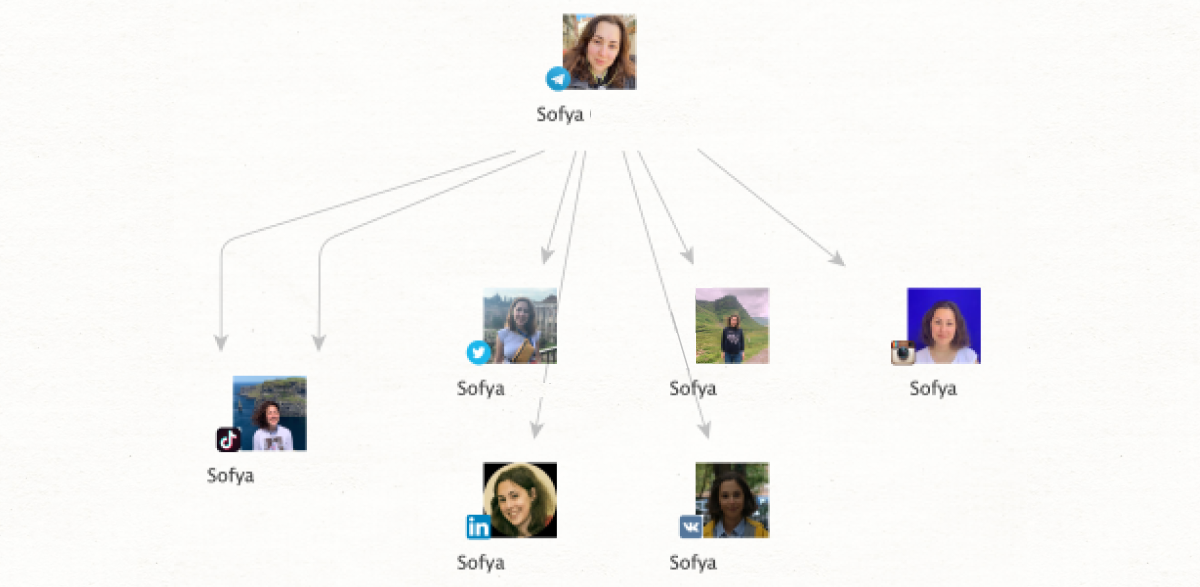
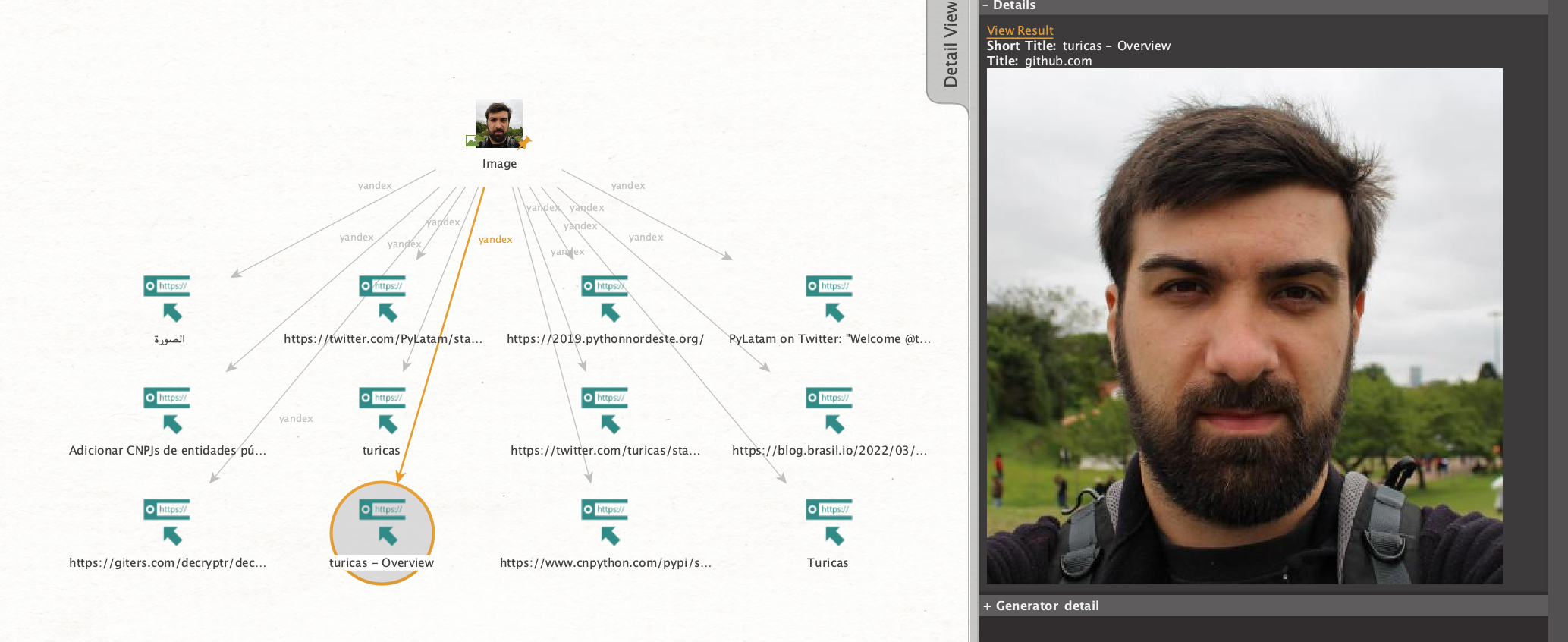
Sometimes, the only input data at our disposal is an image. [Image] Reverse Search search method allows users to elaborate a wealth of information from a single picture, making it an essential first step in many investigations.
Say we have a social media profile picture but nothing else. The picture in question is a nameless man wearing a black t-shirt. From an image entity, we run the [Image] Search in Google method, and the system returns results of enumerable men in black t-shirts that are not actually connected to our person of interest.
By running [Image] Reverse Search instead, we now get a range of results for that particular image, showing all the online locations where it appears. These could be links, articles, or social media profiles – all giving several opportunities for further expanding the digital footprint. In some cases, it will even return different pictures that match the biometrics.
Most social media users are aware that the platform is open source. This means that people may take measures to hide their connections, especially if it is someone they would rather remain secret. For the user’s convenience, social media provides the ‘Hide Friend’ option, which means the connection in question will not be visible through typical searches.
However, we have developed a search method – unavailable on many other OSINT tools – which is a truly important feature because it is sometimes the case that social media users hide their entire friend list. So, this method can change a profile from a dead end to an open book like any other unobscured profile.
Simply run Get Visible Friends from a social media profile entity, and the results will be the ordinary list that everyone can see. Next, we select all of these friends and mark them with a flag, then run our Get Hidden and Visible Friends method. We can now see new friends that have suddenly appeared which are unmarked. These are the contacts that the user chose to hide and may be extremely useful for the next step of our investigation. If the profile in question has hidden their entire list, then you can just run Get Hidden and Visible Friends to view all friends.
Viewing a subject’s friend list is all well and good, but sometimes we need more nuances. Many of these connections are probably people our subject barely interacts with. Conversely, there are also likely to be profiles that the person of interest does interact with but which are not even on the friend list.
In fact, there will be a whole spectrum of interaction from nothing at all to… the sky’s the limit. The beauty of this method is that it breaks this information down so users can see who the subject interacts with and to what extent.
From a social media profile, we run the search method Search Relations. The results will include all profiles that our subject has interacted with, be it a post on a news feed, a comment on a post, or even a simple like. But we can also see that these entities are circles of different sizes. This corresponds to the profile’s ‘weight.’ In other words, the bigger the circle, the more interaction occurs.
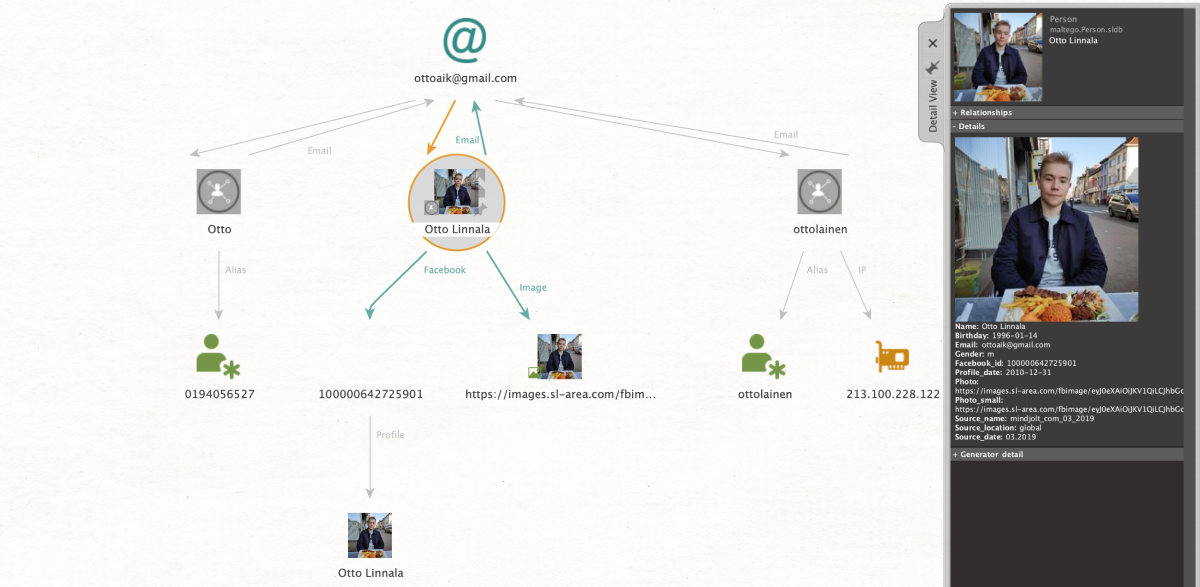
This is an exclusive source Social Links provides, which contains a wealth of material of varying kinds, including names, email addresses, home addresses, IP addresses, social media profiles (of both popular and outmoded platforms), phone numbers, aliases, and much much more.
This OSINT method can be run from many entities (alias, email address, person, phone number, IP address, social media profile, and more). But let’s say we just have an email address. After applying the search method [SL ISE] Search, the system usually returns a few separate results. Next, we select all and run [SL ISE] Extract Entities, and we now see a whole selection of familiar entities from which we can develop the investigation.
These are two simple methods, yet they can prove essential in certain investigation types. [LinkedIn] Get Current Employees discloses everyone employed at a given company at that time. Meanwhile, [LinkedIn] Get Past Employees will show everyone who has previously worked at the organization but has now left. These can be handy in conducting better due diligence on an individual but can also help find potential corporate data leaks and possible instances of fraud.
So, let’s say we are working for a company who have recently agreed on a procurement tender. However, the security team suspected the organization could contain a shadow puppet with ties to the winning vendor. By running these OSINT methods from client and contractor company entities, we can immediately check for personnel connections between the two, encompassing the entire history of both organizations.

When open-source intelligence methods scour social networks for given profiles, they ordinarily do this through the platform’s internal search engine. This has its advantages because it can provide more focused results. The downside, however, is that it is not a very diversified approach.
The benefit of this feature is that, in harnessing Google as the search engine of choice, the results differ from what the standard approach delivers. This means that an investigator can see things from alternative angles. Such OSINT techniques can provide new leads when a particular line of inquiry seems to have dried up. Also, Google retains data that might have vanished from the platform itself, in particular about recently deleted accounts. Likewise, this can make all the difference.
The function has to be run from either a Person or Company entity and offers various search methods for various sources, including all major social media platforms and blogs, Asian social networks, companies, dating sites, GitHub, and media hosting communities.
If any of these search methods are new to you, try them – they are all easy to apply but can make a huge difference to your work, helping you achieve all sorts of investigative goals.