What Is Open-Source Intelligence (OSINT) in 2025?


As we navigate the shifting threat landscape of late 2024 and 2025, characterized by generative artificial intelligence, a splintering digital commons, and the blurring of online and physical risks, the role of Open-Source Intelligence is not just growing—it is transforming into the primary sensor for understanding our world.
This article provides a whistle-stop history of OSINT’s evolution over the 21st century up to the present, and offers a contemporary definition of the discipline through the viewfinder of real-world case studies and challenges facing practitioners today.
For anyone within the intelligence, security, and investigations communities, Open-Source intelligence (OSINT) has become a foundational term. Yet, to define OSINT merely as "intelligence derived from publicly available information" is like describing a modern battleship as simply "a boat."
While technically true, this definition fails to capture the discipline's complexity, technological sophistication, and huge importance as a pillar of national security, law enforcement, and corporate strategy. OSINT is not a passive act of collection; it is a structured, multi-layered methodology for turning the overwhelming noise of global data into verifiable, actionable intelligence.
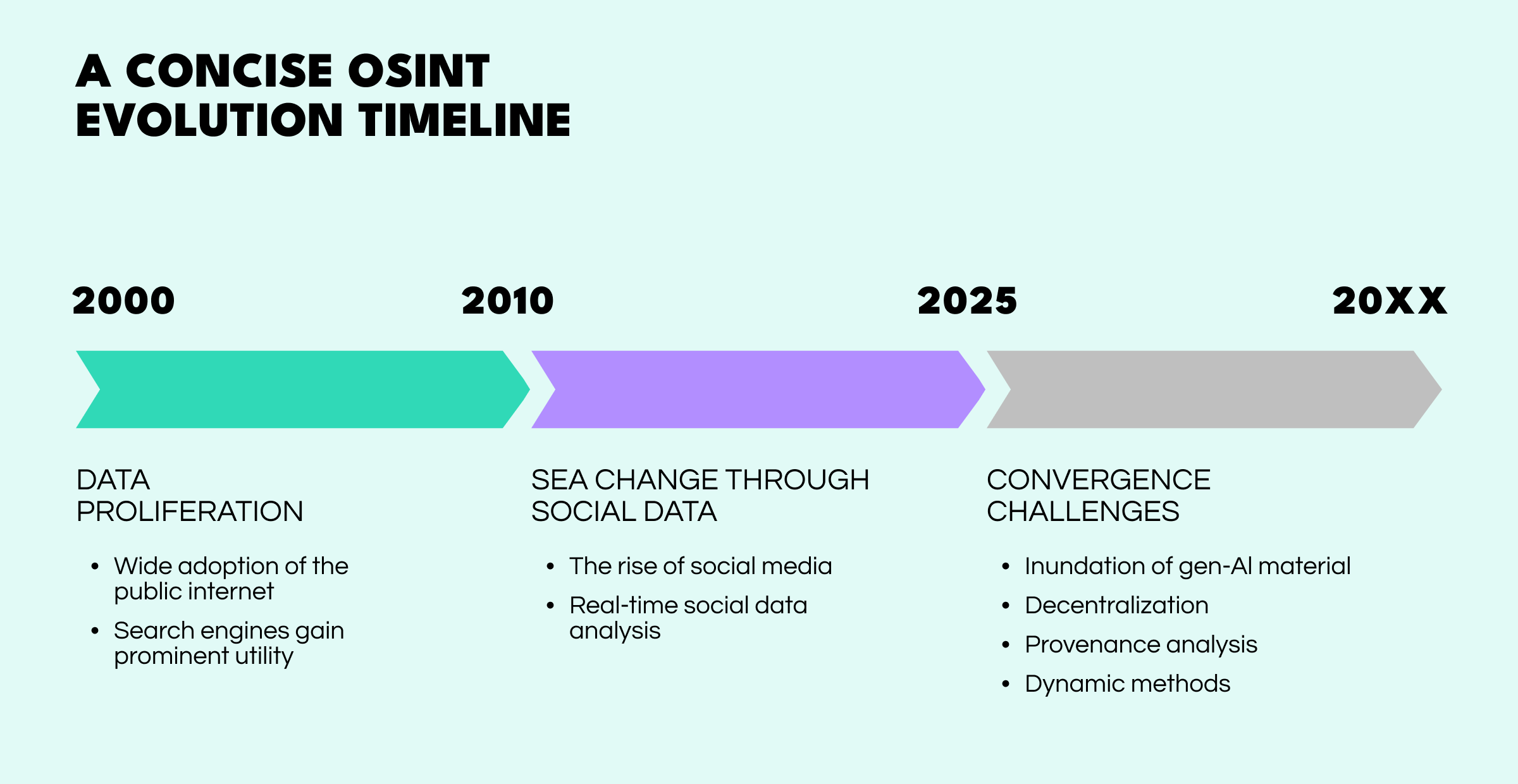
The practice of deriving intelligence from open sources is as old as espionage itself, historically rooted in analyzing foreign newspapers, academic journals, and radio broadcasts. However, the digital revolution triggered a paradigm shift, unfolding in distinct stages that have progressively increased the discipline's complexity and power.
The initial explosion of the public internet and search engines marked the first major transformation. Open-Source Intelligence became synonymous with advanced search techniques ("Google dorking"), website analysis, and digging through public records databases. The challenge shifted from finding scarce information to sifting through an abundance of it. This era defined OSINT as the skill of the master searcher, capable of finding the digital needle in a global haystack.
The rise of social media platforms created a new, dynamic, and deeply personal layer of open-source data. This gave birth to Social Media Intelligence (SOCMINT) and specialized OSINT tools. The focus expanded from static web pages to real-time human activity. Through data collection, analysts could now track events as they unfolded, map social networks, and gain unprecedented insight into public sentiment and group dynamics. This was no longer just about finding documents; it was about understanding people and networks in motion.
The true meaning of Open-Source Intelligence is best understood not through definitions, but through its application in high-stakes scenarios where it provided the critical path to the truth.
The work of the investigative group Bellingcat following the 2014 downing of Malaysia Airlines Flight 17 is the gold standard of modern OSINT. When official narratives were conflicting and opaque, Bellingcat analysts turned to the open-source world, and meticulously scoured social media for photos and videos of a Buk missile launcher moving through eastern Ukraine, posted by local citizens.
By geolocating these images—cross-referencing road signs, buildings, and even the position of the sun with satellite imagery—they traced the launcher's exact route to a field south of Snizhne. They then found a contrail photo taken from Torez that, when triangulated, pointed directly to that launch site.
This was not a single discovery; it was the painstaking synthesis of dozens of independent, public data points through advanced OSINT techniques to establish a verifiable ground truth that later informed official international criminal proceedings.
The Panama and Pandora Papers investigations demonstrated OSINT's power against complex financial secrecy. The initial data emerged through a leak, but the real work was the OSINT that followed.
Journalists and investigators deployed OSINT techniques to connect the names of shell company owners found in the leaks to their real-world lives. This involved cross-referencing names against public corporate registries, property records, and court documents. Crucially, they used social media to map family connections—finding a politician’s son flaunting a lavish lifestyle on Instagram funded by a company secretly owned by his father.
This is deep OSINT: weaving together leaked data with public records and social intelligence to pierce the corporate veil and expose illicit wealth.
In the wake of the January 6th, 2021 attack on the U.S. Capitol, law enforcement faced the monumental task of identifying hundreds of individuals from a chaotic scene. The FBI's effort was massively augmented by an unprecedented, crowdsourced OSINT campaign.
OSINT researchers, investigative journalists, and regular citizens sifted through a deluge of information, collecting data from platforms like Parler, Facebook Live, and YouTube. They used facial recognition on live-streamed videos, identified individuals by unique clothing or tattoos seen in photos, and cross-referenced usernames with other social media profiles to build comprehensive identity profiles.
This was SOCMINT at a massive scale, demonstrating that in an age of ubiquitous self-documentation, every public action can leave an indelible digital trace.
The challenges of the past are now converging with new technologies to create a more complex and dangerous threat environment. To remain effective, OSINT practitioners must contend with three major shifts.
The rise of machine learning has had a huge impact on the digital landscape. The proliferation of high-fidelity deepfakes and gen-AI text means that the foundational OSINT principle of "trust but verify" is shifting to "distrust and meticulously corroborate". An image or video can no longer be taken as prima facie evidence.
The OSINT of 2025 is increasingly focused on provenance analysis—using a combination of digital forensics and cross-platform signal correlation to determine if a piece of media is authentic. The key skill is not just finding and collecting data, but validating its origin.
Users are migrating from monolithic public squares like X (formerly Twitter) and Facebook to a constellation of semi-private, ephemeral, and decentralized platforms like Telegram, Discord, and Mastodon. This "splintering" means that intelligence is no longer concentrated in a few easily accessible places. As a result, OSINT data collection now requires more sophisticated, adaptable methods capable of navigating these fragmented ecosystems and keeping track of a new more slippery breed of threat actor.
The barrier between online rhetoric and real-world action has dissolved. Disinformation campaigns directly incite physical violence, and online radicalization leads to domestic terrorism. OSINT is the connective tissue that links the digital chatter to physical risk and security vulnerabilities, making it the essential tool for early warning and threat assessment for law enforcement and corporate security teams alike.
OSINT has evolved from a niche skill of information retrieval into a core strategic discipline of information synthesis. Its modern meaning transcends the "open-source" tag to encompass the complex art of navigating a digital world of questionable authenticity and fragmented communities.
As we look to 2025 and beyond, the value of OSINT will only intensify, and it will be the ability to cut through the noise of gen-AI content, bridge the gaps between splintered platforms, and connect digital signals to physical threats that will define effective security and a range of operations deployed by the intelligence community.
Success will not be determined by access to data, which is ubiquitous. It will be determined by the sophistication of the analytical frameworks, the effectiveness of the OSINT tools used for gathering and analyzing and, most importantly, the skilled human analyst who can perceive the patterns, validate the sources, and synthesize disparate data into a coherent narrative.
In this new era, the OSINT professional is not merely a searcher; they are the essential sense-maker in a world of overwhelming information.
OSINT (Open Source Intelligence) refers to the process of collecting, analyzing, and synthesizing information from publicly available sources, such as websites, social media, news, and public records, to produce actionable intelligence.
There is no difference. OSINT is simply the abbreviation of Open Source Intelligence. Both terms describe the same discipline.
In 2025, OSINT is essential because of the rise of generative AI, deepfakes, and fragmented digital platforms. Security teams, investigators, and the intelligence community rely on OSINT to validate data, detect threat actors, and bridge online and offline risks.
OSINT tools are software platforms, search engines, and frameworks that help analysts collect data, track IP addresses, discover security vulnerabilities, and support intelligence gathering at scale.
Typical OSINT techniques include advanced search queries (“Google dorking”), social media monitoring, IP address tracking, geolocation, metadata analysis, and machine learning–assisted validation.
OSINT is widely used by law enforcement, journalists, corporate security teams, and independent OSINT researchers. It has become a vital resource for uncovering hidden networks, monitoring threat actors, and supporting investigations.
If you'd like to discover for yourself why Social Links are considered an industry-leading provider of OSINT solutions, follow the button below and we'll set up a personalised demo with one of our specialists, where you can see how our products can deliver on all of your OSINT needs.