Center of Excellence Column: DNA Analysis in OSINT

This week in the Social Links Center of Excellence Column, we’re diving into using DNA as a resource for open-source intelligence. This time, we will share ways and techniques to use biological identifiers when revealing suspects and building a case.
So, let’s move to the investigation!
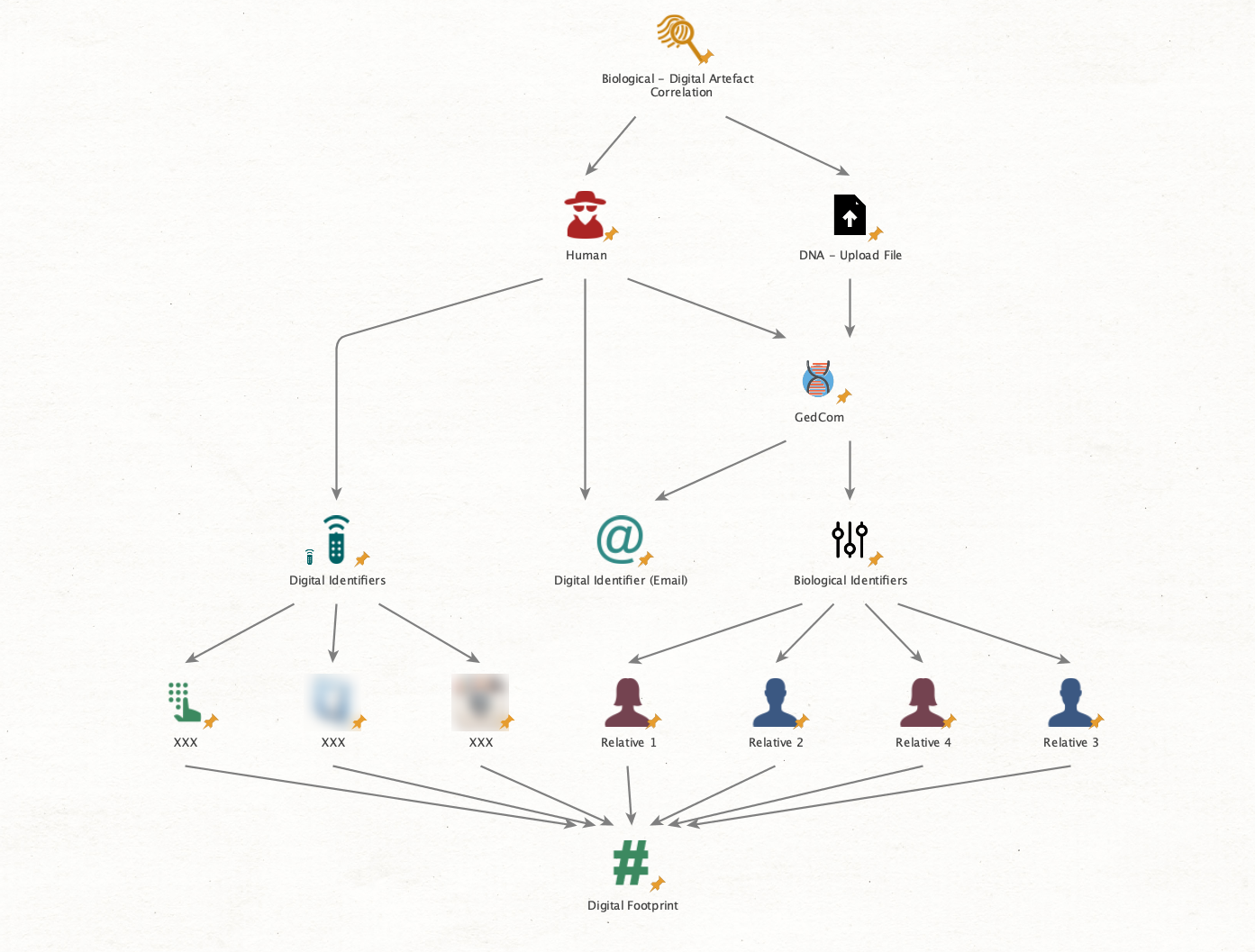
Our investigation begins with a set of "GEDmatch Kit" entities we've sourced from an email. The workflow involves multiple steps, including data extraction and executing a "GEDmatch" lookup query on the source information. To set the stage, we're leveraging GEDmatch, a powerful resource that played a pivotal role in solving the infamous Golden State Killer case.
We're equipped with numerous GEDmatch kit entities, which serve as our starting point. These nodes contain vital data that we intend to extract. The investigation hinges on the correlation of DNA datasets with friends and individuals who have interacted with the subject under investigation. To achieve this, we identified some full names and initials that came up during our inquiry. Once we enrich the digital footprint of the individual, we can discern connections with other ones.
We start creating the digital footprints of the individuals through their emails under scrutiny. Examining the properties of these GEDmatch kit entities, we've observed that individuals have mostly shared their email addresses while uploading data about themselves and their relatives into the system. The initial point of access was via the email address "greg@helioart.org," but that’s not all we have. There are several additional aliases tied to these entities, including G. Spitz, GS, JK, CS, and KK.
To streamline our investigation and maintain focus, we have utilized the standard functionalities associated with email data. Our main objective is to access one of the individual's social media accounts, with a preference for LinkedIn. This platform is a gateway to understanding the subjects’ digital footprint more comprehensively. Additionally, we aim to identify any connections between these individuals on the graph generated from the initial GEDmatch kits.
Armed with the email entity "greg@helioart.org," we could successfully access the person's LinkedIn profile. This provided us with a wealth of general information on the subject, including current position as CPO at Helio Art, educational background at the University of California Santa Cruz, and location in Del Mar, California, United States. Further, we revealed their social media profiles, which provided us with more relevant insights into the suspects' real-life connections.
The discovered information helped us gather details about their relatives and examine their friends lists. We employed two distinct methods: "Get Visible Friends Fast" to acquire visible friends from the profile and the conventional method to get the complete friends list. Close examination of suspects' posts led to more detailed information about the individual, including interactions with other users. The same principles are also applicable, albeit to a lesser extent, on Twitter and LinkedIn.
After in-depth research, we identified several individuals. These included a person assumed to be a relative named Abigail Spitz, Amanda Warren Spitz, and others. Another valuable tool we've employed is the phone number associated with the people entity, often leading to the acquisition of phone numbers belonging to the individual's relatives and close associates.
Our investigation has allowed us to identify similarities among various individuals, including Greg Spitz and others previously linked in a graph connected to Richmond. This data has further strengthened our understanding of these individuals and their connections. Notably, they all share an address on the Del Mar Scenic Parkway in Del Mar, California, as evidenced by the graph. Additionally, we've encountered another person, Cristoff Spitz, previously denoted as "CS" on the graph.
Illustrating the investigative process, consider the case of William Creed. Through our inquiry, we identified many relatives associated with William Creed. This led to the discovery of his profile on Skype, which further enabled us to access his other social media accounts. From there, we extracted friends and identified Jessica Creed, William Creed's wife, establishing a concrete connection with him on GEDmatch and social media platforms.