Center of Excellence Column: Stepping Up Perimeter Surveillance with OSINT


This week in the Social Links Center of Excellence Column, we’re diving deep into increasing an organization’s cybersecurity state with OSINT. Since the benefits of open-source intelligence for cybersecurity are often discussed, we created a case study to show exactly how it’s possible.
Let’s jump into it!
Meet the main character of the case, Mark Turner. He’s the chief information security officer (CISO) in the WiredCorp company. Mark has to develop a system for ongoing perimeter defense for the organization, which will protect WiredCorp from threat actors. Luckily, he has a background in open-source intelligence and knows how to use various data sources. He creates a system that uses proactive and reactive intelligence techniques at the same time:
Both of these methods involve the application of cyber threat intelligence. Basically, Mark gathers information about potential dangers and makes sure the system is protected against them. Typically, doing all of this research manually is time-consuming. However, OSINT tools streamline the processes to ensure the ongoing safety of the system.
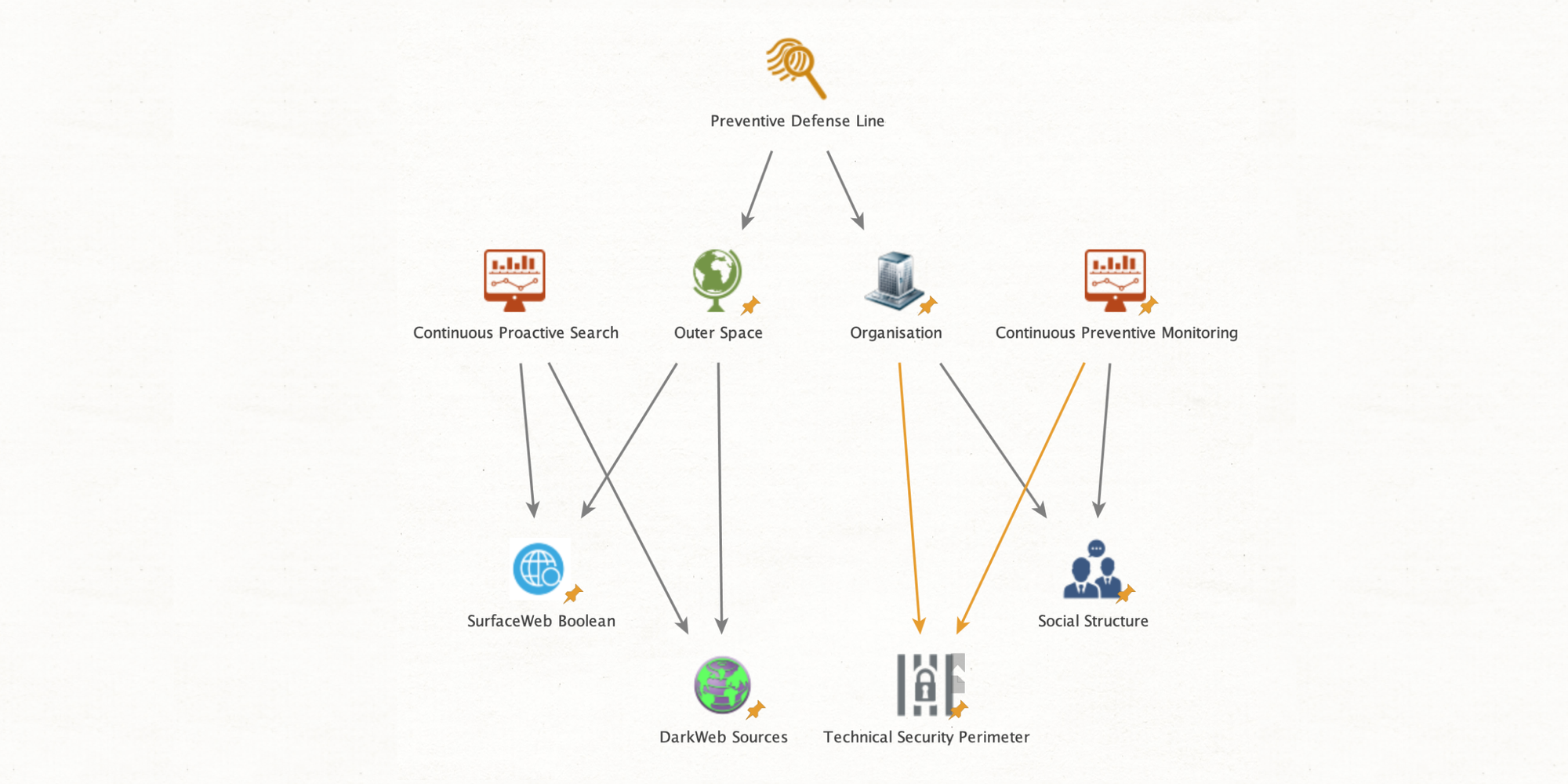
Surveying the organization's existing employees is a powerful way to prevent insider threats. That's why Mark starts with a comprehensive examination of the people within the company. The goal here is simple: uncovering affiliations with competitors, identifying abnormal behavior, and detecting any potential involvement in illicit activities. The security check involves sources such as social media platforms, corporate repositories, and facial recognition databases.
In addition to employee safety, this step also requires analyzing the technical security perimeter. Scrutinizing things like company IP addresses, hostnames, security certificates, and GitHub content is critical. However, doing all of these actions requires using tools like Censys and WhoisXML.
Let’s clear up any potential confusion. The tools mentioned above gather technical information about a company's online security. Censys searches and analyzes data on web hosts and networks. WhoisXML, on the other hand, focuses on domain information, such as ownership and registration data and DNS records.
So, after all of this analysis, Mark can get a clear understanding of the company’s technical assets like domains, public file storage locations, the amount of sensitive data they have, and if there are any security vulnerabilities.
The darknet is an excellent source of information for identifying the activities and plans of malicious actors and gaining cyber threat intelligence. The past actions of cybercriminal groups can inform their future attacks as well, so it serves as a crucial sphere to be aware of.
Investigating darknet sources often results in valuable leads that can help specialists secure their organization against dangers. Compromised confidential information and leaked employee credentials are only some of the things experts can discover in this sphere.
Scanning the visible Internet involves a more traditional approach. Looking up social media accounts with a tool like SL Crimewall speeds up the process significantly. Moreover, using sentiment analysis provides investigators with an efficient way to reveal negative mentions, threats to employees, and disinformation against the organization WiredCorp.
The Surface Web analysis involves a constant back-and-forth between the other two steps, so it covers much of the moment-to-moment analysis of Dark Web monitoring and in-company scrutiny.
To summarize the whole process, the security specialist Mark Turner set up a system that proactively analyzes the Dark Web, Surface Web, and in-company assets. This methodology aimed to identify potential threats before they become an issue. With the clever application of OSINT solutions, Mark created a robust system for his company to safeguard the infrastructure and secure the organization against future malicious attacks.