Center of Excellence Column: IP Address Analysis in OSINT Investigations

In this week's Center of Excellence Column, we present a case study about deanonymizing an online suspect who conceals their name. We use IP analysis and OSINT techniques to gather data, illustrating unique methods to reveal the identity of a potential pedophile.
So, let’s jump into the investigation!
Disclaimer: For privacy reasons, we have changed all the names involved in the original situation.
Our case starts with a TOR (The Onion Router) exit node IP address. We don’t have the name of a suspect (yet), but the input suggests that the threat actor is trying to hide their online activities. This is the part where we’re getting technical.
When we analyze the IP, it leads us to several GitHub repositories. In addition, we find the netblock, a collection of IP addresses that share a network, and the ASN (Autonomous System Number), which groups and identifies related IP networks that share a standard routing policy on the internet. Finally, we get a match on the SL ISE (Identity Search Engine) matching the IP addresses.
So, what does all of this mean? Everything we found involves some sort of registration that gives us clues about our unnamed suspect’s identity. We start cross-referencing all the information (usernames, registration data, and birthdays), which leads us to an email address—psychnote.
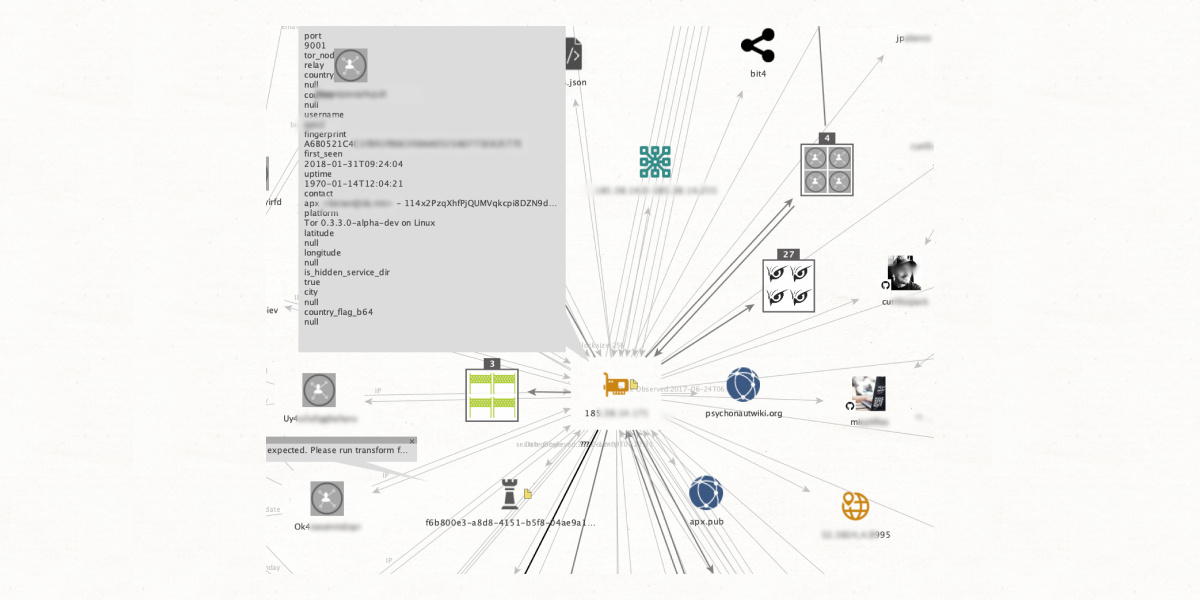
In the next step, we're scrutinizing the previously found email address. One of our matches at this step is another SL ISE node that gives us the associated username “oselateinertia.” Although this alias seems disposable, exploring its activities reveals essential details, such as another email address (oserunner) and two IP addresses.
The first IP address is from the Netherlands, and the second is from Sweden. One of the IPs has a connection to a Pastebin (an online plaintext storage service) with a list of addresses that were tied to pedophile cases. As we delve into these findings, we’re getting closer to our suspect.

The other IP address connects to an email and alias called crazykir7803. When we look into it, we get another match from the SL ISE entities. Luckily, this one confirms that crazykir’s birthday is March (03) 1978. However, the real gem we find is the suspect’s name—Kirsten Briar.
When we start looking into the name, we find a lot of documents from the Dark Web (which we get thanks to the DarkOwl plugin of SL Professional). In these files, we see Kirsten Briar’s activity history on illicit child sexual abuse material forums, along with her phone number, Telegram account with the name Kir, and social media profiles.

Our investigation allowed us to start with only an IP address and use analysis and matching techniques to deanonymize a pedophile. We could cross-reference information by systematically checking every username to reveal non-obvious associations between addresses and aliases to finally locate our suspect.