Top 7 OSINT Tools for Dark Web Investigations in 2023


Fortunately, help is here. In this article, we handpicked the top OSINT tools for combating crime on the Dark Web in 2023. The solutions listed can significantly enrich investigations by deanonymizing criminals, extracting relevant insights, and mitigating the dangers associated with the darknet. Note: all OSINT tools for the Dark Web can fit into any existing workflow and work best when combined with other intelligence methods.
So, let’s get straight to the point.
As criminals constantly try to hide their traces, the darknet is an attractive option for many. With specialized browsers like TOR providing strong encryption, tracking malicious activities becomes challenging but still possible. Specialists equipped with OSINT tools can detect digital footprints and uncover crucial clues for their investigations. Keeping this in mind, let's see what open-source intelligence solutions can reveal.
The Dark Web is a treasure trove for threat intelligence. Many hidden platforms are serving as meeting spots for malicious groups. Experts estimate that around 53k extremist groups use the darknet to plan attacks and raise funds for their operations through drug markets, scams, and more. A recent example from 2015 — the Islamic State of Iraq and Syria (ISIS) is believed to have raised $23M in Bitcoin in one month through the Dark Web.
However, the Dark Web is also the preferred space for hacker groups. Many forums focus on planning and executing cyber attacks on companies and individuals. Surprisingly, 90% of posts on underground forums come from customers looking to hire hacking services. With the right tools and appropriate OSINT know-how, it’s possible to deanonymize malicious actors, collect their digital footprints, and prevent potential cyber or terror attacks.
In one of our previous articles, we mentioned that blockchain solutions are in demand for money laundering. One of these, crypto mixers (or tumblers), are platforms that take large transactions and break them up into tiny transfers. Such interference can significantly obscure the money flow. Recent reports show that in 2022, money from illicit addresses made up 23% of funds that mixers received (in contrast, it was 12% the previous year).
While breakthroughs in demixing crypto tumbler transactions can soon make these services more difficult to use, it’s not the case yet. Official figures reveal that mixers are more popular than ever, with $51.8M worth of crypto going through these services in April 2022. To complicate the matter more, many Decentralized Finance (DeFi) projects aim to replace tumblers, which can result in new challenges for investigators when dealing with financial crimes. Luckily OSINT tools can trace transfers through mixers, which enables investigators to deanonymize criminals.
The Dark Web is home to a lot of illicit things. One of the most famous (or infamous) goods on the platform is drugs. This was highlighted in 2023 when investigators brought down Monopoly Market and seized $53.4M, 850 kilograms of drugs, and 117 firearms in raids across several countries. However, combating criminal marketplaces is extraordinarily time-consuming and usually spans multi-year investigations. In such cases, OSINT solutions provide an edge for specialists, as they can significantly boost productivity and cut down on time.
Another global concern connected with the Dark Web is the distribution of child abuse material. In 2022, the US National Center for Missing & Exploited Children (NCMEC) received 32M reports of such cases. Sadly, many encrypted underground websites share or sell videos of child exploitation worldwide. However, the developments are not all bleak, as Europol assisted in taking down the notorious “Boystown” darknet forum in Germany, infamous for sharing child abuse content and having 400k registered users. Many agencies worldwide use OSINT solutions to put an end to such platforms.
There are many moving parts when investigating the Dark Web, which creates many challenges. That is why experts employ various tools to handle the workload. Meet our list of the top OSINT tools on the Dark Web we compiled for different use cases. From deanonymizing criminals to gathering evidence for an investigation, these solutions can help boost existing workflows.
Our top pick is a full-cycle, standalone OSINT platform. With access to more than 500 open sources and 1700 search methods, Crimewall allows investigators to thoroughly scan and analyze both the Surface and the Dark Web to deanonymize suspects and get a complete picture of the investigation.
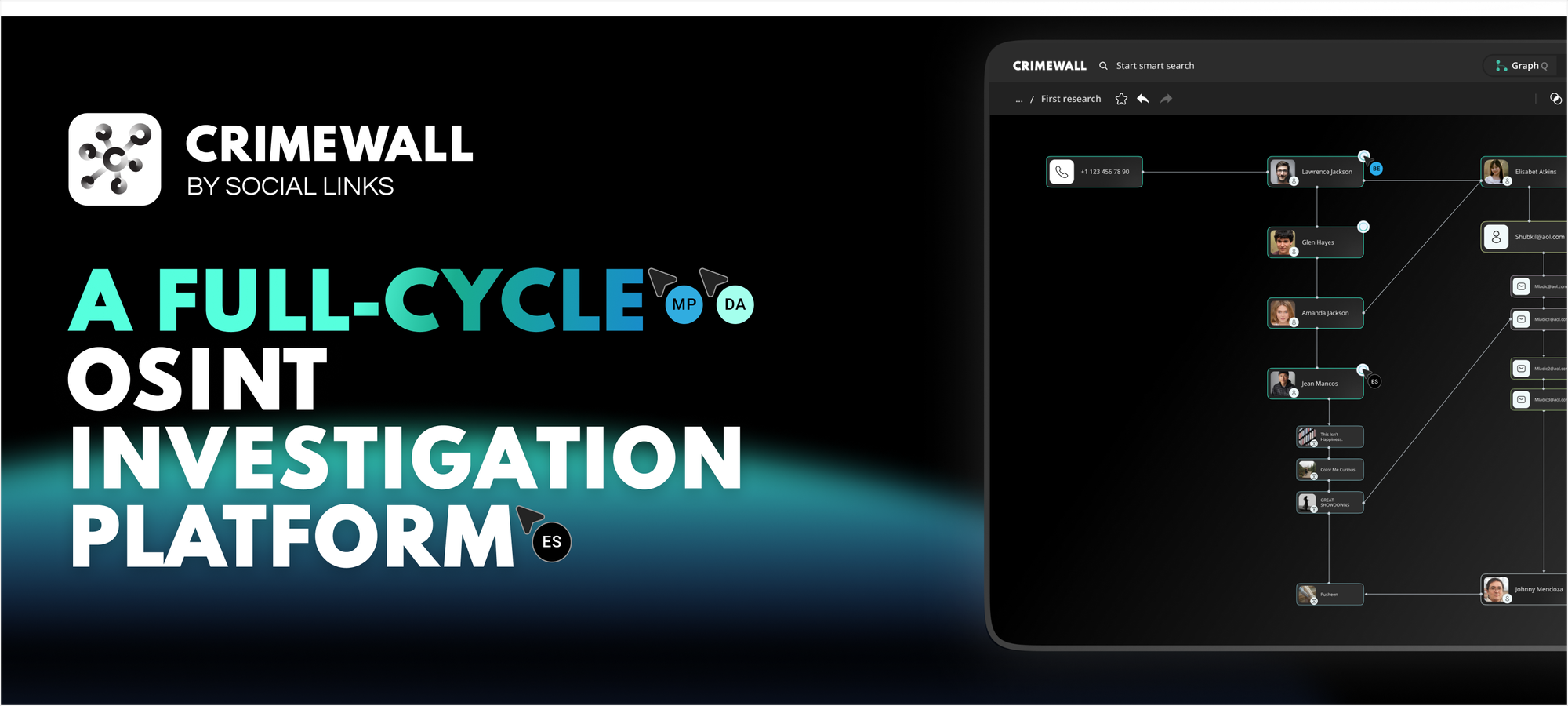
Product Features:
The second tool is focused on uncovering all the hidden elements of the Dark Web. With the robust scanning functionality, users can monitor, browse, and stream content in near real-time from the Deep Web, darknet, and authenticated chat platforms.

Product Features:
The third pick is a solution by Authentic8, which focuses on mitigating the risks of researching shady online spheres. As a secure web browser environment built for researchers and analysts, the tool prioritizes safeguarding against malware and improving privacy when exploring the Web.

Product Features:
Next is an advanced search engine designed to provide access to a wide range of data sources on the Internet, including the Deep and Dark Web. Intelligence X allows users to search and analyze email addresses, phone numbers, and more to better understand digital footprints for enhanced decision-making.

Product Features:
This powerful intelligence platform empowers organizations to gather, analyze, and act on critical information from the Clear and the Dark Web. The tool provides comprehensive monitoring capabilities and real-time alerts to stay informed about emerging threats and incidents.

Product Features:
The following solution is a robust web capture tool designed for investigative professionals. To streamline specialists' workflow, Hunchly helps users backup, organize and search for web pages and social media profiles encountered throughout the inquiry process from both the Surface and Dark Web.

Product Features:
Last but not least, this cutting-edge cybersecurity platform provides comprehensive threat intelligence and monitoring capabilities across the Surface and Dark Web. Darkscope’s tool enables organizations to stay one step ahead of malicious actors by identifying system vulnerabilities, protecting critical assets, and responding to cyber incidents.

Product Features:
And that’s our list of top OSINT tools for Dark Web investigations! While these solutions will be most effective when combined with other software, our list is an excellent starting point for building a practical investigative base. For more OSINT knowledge, be sure to sign up on our blog.