8 Nonobvious OSINT Methods to Boost Any Case


We recently published a guide to some of the most essential SL Professional methods every investigator should be taking advantage of. However, essential though these search queries are, the solution has much more to offer, and if you get set in your ways, it may be limiting or even counterproductive. Better to shake things up and try new techniques.
So, welcome to our review of 8 not-so-obvious Social Links OSINT methods! These are super handy tricks for analysts to have up their sleeves, and which could easily make the difference between a dead end and a breakthrough. Whether you’re an old hand or new to SL Professional, these approaches will give you a wider investigative range.
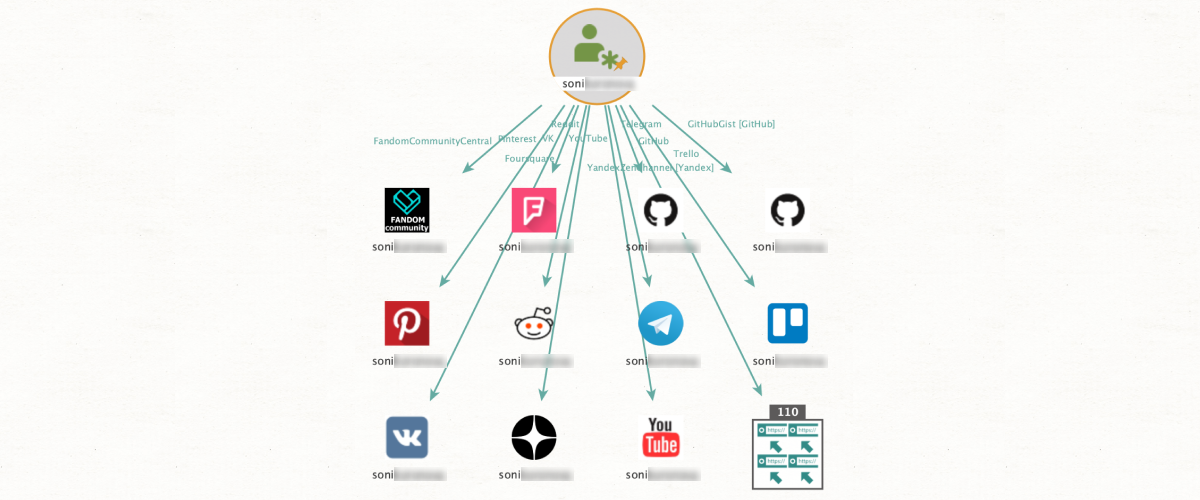
Social Links OSINT methods are known for their incisive and in-depth search capabilities. But we have also developed methods that are remarkable for their expansive breadth, of which this is a good example.
With just a few clicks, the user can extract a given alias from 500+ open sources from major social media platforms including Instagram, Twitter, and the like, to more niche online accounts such as Etsy, Trello, Duolingo, Giphy, etc. The benefit of this method is that it allows investigators to quickly elaborate a rich digital footprint and gain a broad picture of the subject.
So, we start with an alias entity and enter the appropriate text – for instance, ‘mikedenver’ – then run the method [Alias] Search in Sources. The system will return all accounts which have that exact username, NOT including similar variants such as 'mike_denver' or 'mikedenverr'.
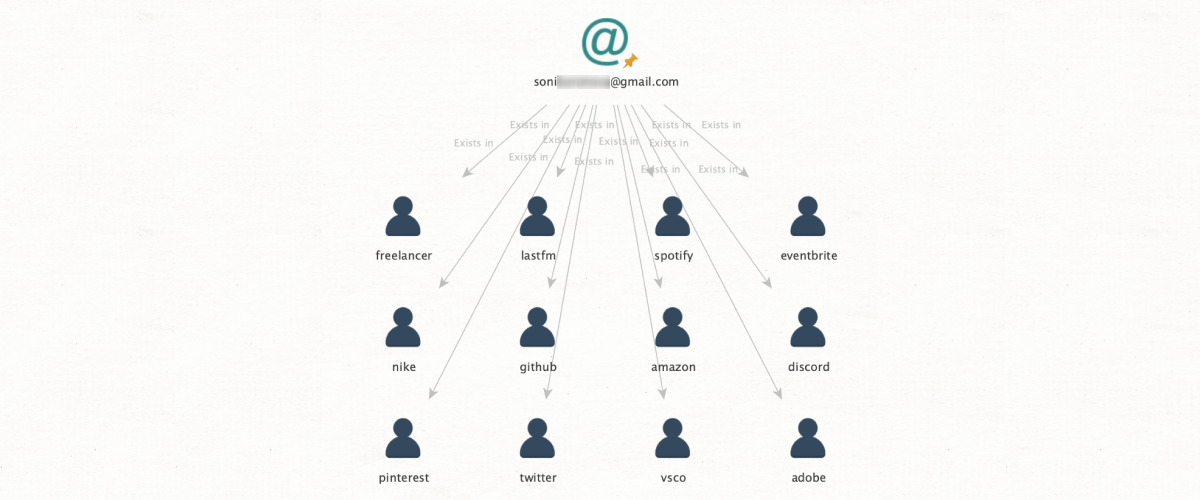
The essential benefit of this method is that it greatly saves the investigator’s precious time. Put simply, it allows the user to verify the existence of all social media accounts connected to a given email before they go through the process of actually trying to locate the profile itself. There are two main approaches.
Approach one. Let’s say we have an email address and you just want to check what social media accounts are connected to it, to focus subsequent searches. We just have to run [Email] Check Profile Exists from the email entity, and we will see all platforms – for instance, Instagram, Discord, etc. – which you can expect to find a relevant user account.
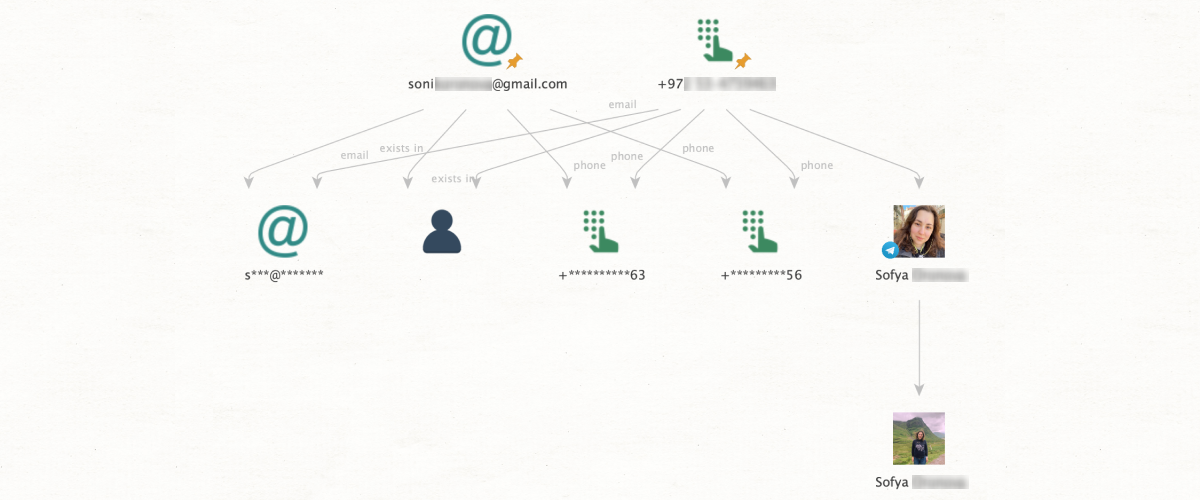
Approach two. This time we have a phone number and an email address, which we suspect belong to the same person. However, we can’t be sure, so verification is needed. From an email entity we can run Check Profile Exists. This method will not only return a result for a social media profile, but can also provide additional OSINT data. If a profile does exist, we will also be able to see the last two digits of the account phone number as it is displayed for password recovery purposes, for instance: ***-**-55.
Now, if our suspected phone number ends in 55, we can be quite confident that it does indeed have the same user as the email in question. Finally, it should be noted that the subjects will remain unaware that their profile has been viewed in this manner – they will not receive any notifications or indications that these details have been accessed by another party.
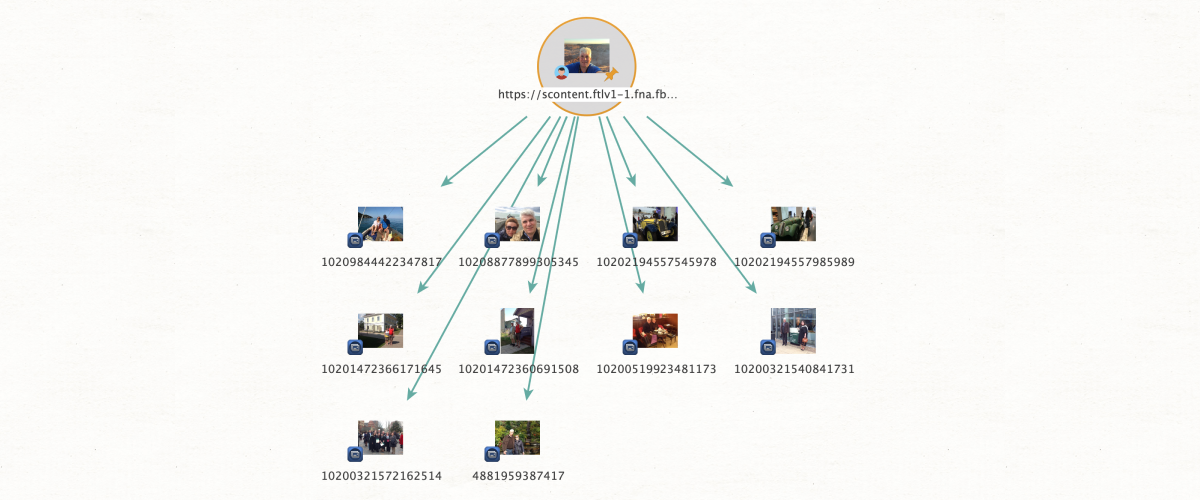
This method is great for establishing connections (especially when people intentionally hide them). From an image input, facial recognition algorithms apply biometric data to find the same individual from among the photo gallery of a chosen social media profile. This is particularly helpful in cases where the subjects in question are not friends in social media but do actually know one another.
For instance, we have a picture of Person A who we want to identify among the photo library of a social media profile connected to Person B. We start by entering the necessary input data– we need a URL directly linked to the image for the photo input, and the social media profile requires either a profile URL, a user ID, or an alias. Once we’ve added the appropriate data, we just apply Search by Face and Profile to get our results, which will show all photos from the profile of Person B that contain Person A.
This is designed around a similar premise to the method above but with a different focus. It uses a photo to establish whether or not this person is a member of a given social media group, providing it isn’t closed. This might be helpful if, for instance, we're searching for potential extremists or violent protesters.
As above, we enter our data into an appropriate entity from which we then run the method Search by Face and Group Member to get our results. Note that this method searches through the current profile photos of the group members as opposed to the photo gallery of the page.
People have a tendency to reuse passwords for different logins. So, we’ve created a method that makes ingenious use of this fact to help investigators find a common actor behind separate accounts. This can be particularly useful in criminal cases that hinge on linking accounts found on the Dark Web to those on the Surface Web.
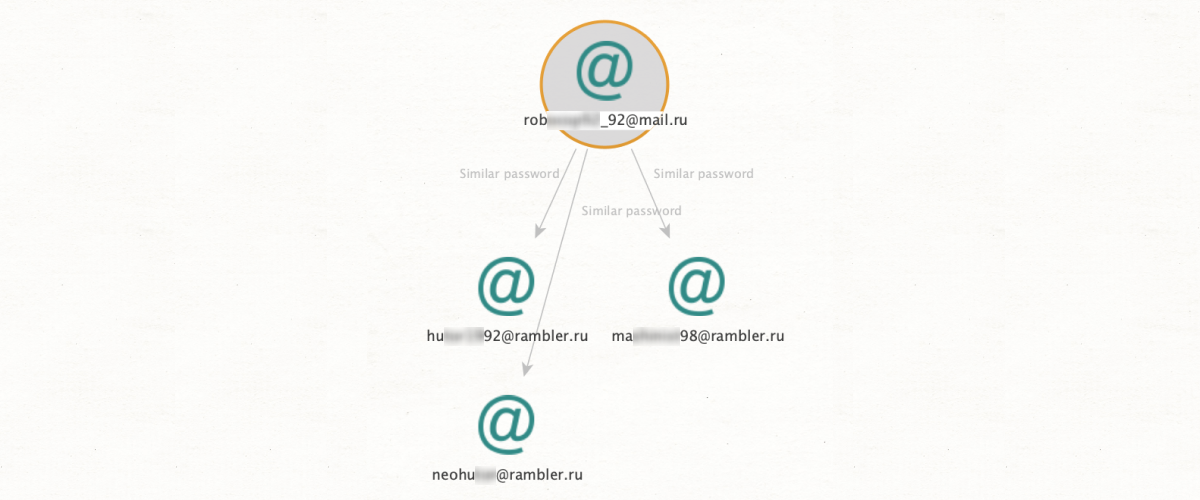
Let’s say we’ve found an email address on the Dark Web, and we want to deanonymize the owner. We simply run the method [SL ISE] Search Email with Similar Password from an email entity. SL Professional will return all profiles which share the same password – or one that is very similar. The results could include all kinds of Surface Web profiles from mainstream social media platforms to little-known online stores, providing the investigator with crucial material for identifying the subject.
Something to bear in mind: The solution will only return results if the password is sufficiently uncommon. For instance, commonplace entries such as ‘qwerty’ will be far too numerous to be of much use, so these results will not be shown.
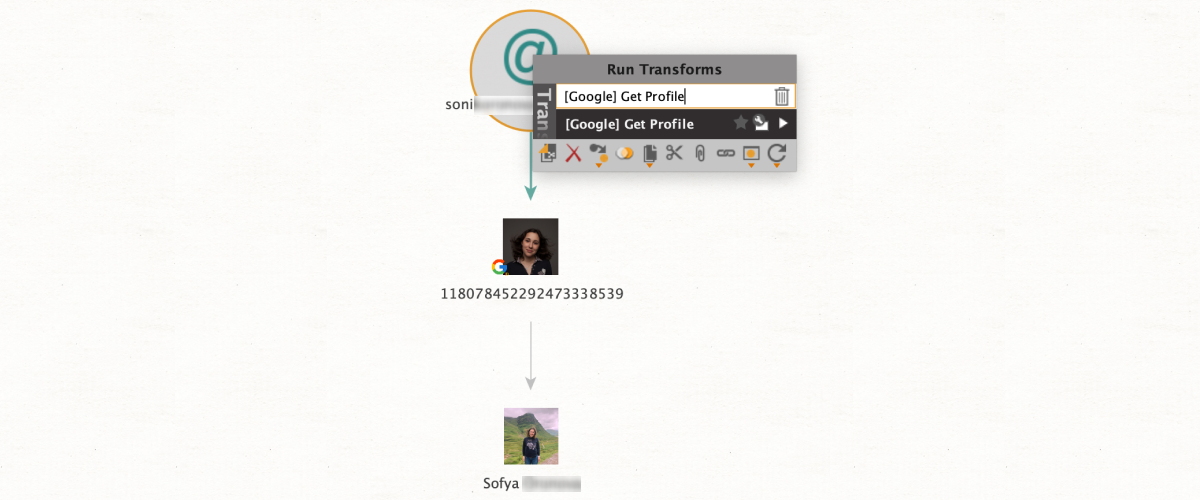
This search query provides a superb way to get a case going from minimal input data. Starting with just an email address, the user can extract crucial OSINT data on a subject that can then be used as a point of departure for a much more in-depth investigation – all in one short step.
So, we have an email address. All we need to do is run [Google] Get Profile from the email entity to retrieve the subject’s Google ID, full name, and potentially a photo.
Remember that this method will only return results for email addresses connected to a Google ID.
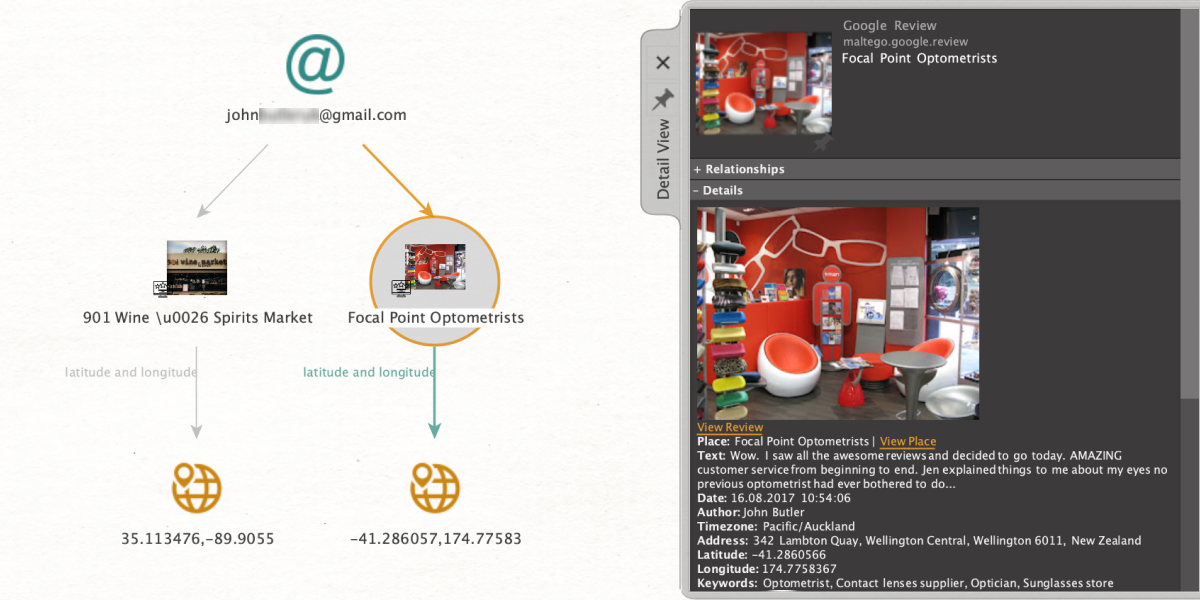
This is a search method that internally relies on the same extraction channels as the previous entry, but delivers different results – namely, details on all the establishments which the subject has rated or reviewed on Google. This can be super useful when trying to map a person-of-interest’s geographical history.
As above, we start with an email entity and apply [Google] Get Reviews. If the email address is connected to a Google ID, we will now be able to view the subject’s name alongside all the places – bars, restaurants, shops, etc. – that have been rated or reviewed by that person. Our results will also include all geolocations in the form of addresses and coordinates.
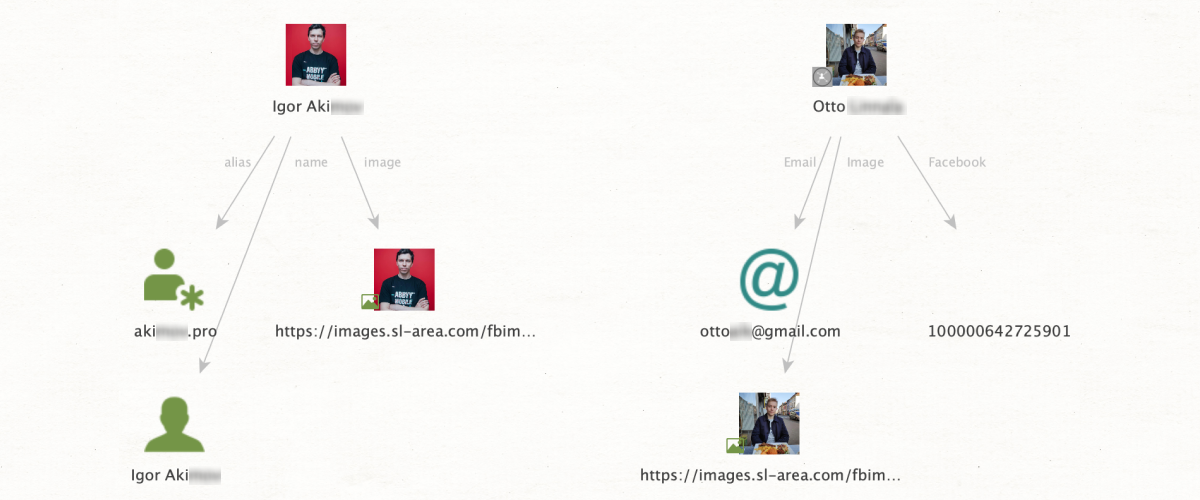
Another classic time-saver, this is a function that all SL Professional users should be benefitting from. Essentially, it enables the analyst to directly export OSINT data from the properties tab as new entities on the graph – no need to go into the entity palette, drag something new into the graph window, enter data, etc, etc. Just a couple of clicks and we’re good to go!
The amount of time that can be saved is immense, especially in cases where we are dealing with large numbers of entities. Also, this feature has an extremely wide application. In principle, any data which can normally be an entity can be exported from the properties tab in this way.
For example, let’s say we’ve just found an Instagram profile which is of interest to us. The properties tab is showing us a photo and an alias, both of which we want to start new searches around. From the Instagram entity, we just run [Extract] Entities and – that’s it! The photo and alias will immediately appear as new entities on the graph, and we can proceed to the next step without delay.
Because this function has such wide usage, the name of the method varies depending on the type of entity the user wants to unpack. For SL ISE entities, the method is [SL ISE] Extract Entities; for Instagram, LinkedIn, Discord, and Twitter entities, we need [Extract] Entities; and finally, for everything else, it’s [Convert] Entities to Profile.
If any of these OSINT methods are new to you, give them a try – they are all easy to apply but can make all the difference in your work, helping you achieve all kinds of investigative goals.